You can make any on-premises web application available via Azure AD App Proxy. The apps can run on any platform (not just Microsoft Windows and Internet Information Server).
IMPORTANT
Azure AD App Proxy requires Azure AD Premium P1 or Azure AD Premium P2.
Configuring an app
You’ve already learned about Azure App Proxy’s capabilities and have installed the connector. In this section, we’ll use it to configure an on-premises application:
- Navigate to the Azure portal (https://portal.azure.com).
- Enter app proxy in the search bar and select Application Proxy from the results or navigate to it via Azure Active Directory | Enterprise applications | Application proxy.
- Select Configure an app.
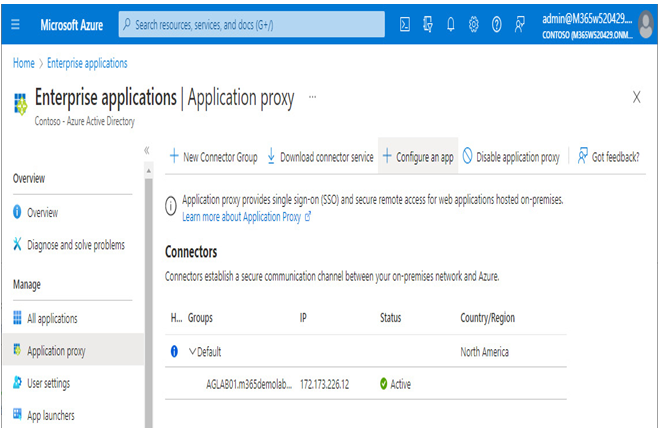
Figure 9.19 – App proxy Configure an app
- On the Basic tab, enter a name for the application (as it will be displayed in Enterprise Apps and on the My Apps page).
- Enter a value for Internal Url. This value must be resolvable and accessible from the server where the Azure AD App Proxy connector is installed.
- Enter a value for External Url. This value, though not mandatory, will allow the application to be accessible directly (instead of requiring users to log in to Microsoft 365 or My Apps first to see it).
NOTE
By default, the domain portion is linked to an Azure AD App Proxy domain name (msappproxy.net), though you can choose any domain registered in your tenant. If you select a public domain you own, you’ll need to configure a DNS CNAME record in your organization’s external DNS to point to the default Azure AD App Proxy value.
While the onmicrosoft.com initial domains do appear in the domain list, Microsoft recommends that you do not choose them. - Select a Pre Authentication method (either Passthrough or Azure Active Directory).
PRE AUTHENTICATION SETTINGS
Pre-authentication determines whether users are verified against Azure AD prior to gaining access to the application. Setting this option to Azure Active Directory means that users are validated against Azure AD first, while setting it to Passthrough means they are not. Only apps configured for Azure AD pre-authentication are eligible to be configured for MFA and conditional access. - Select a Connector Group option.
- When you’ve finished, click Create.
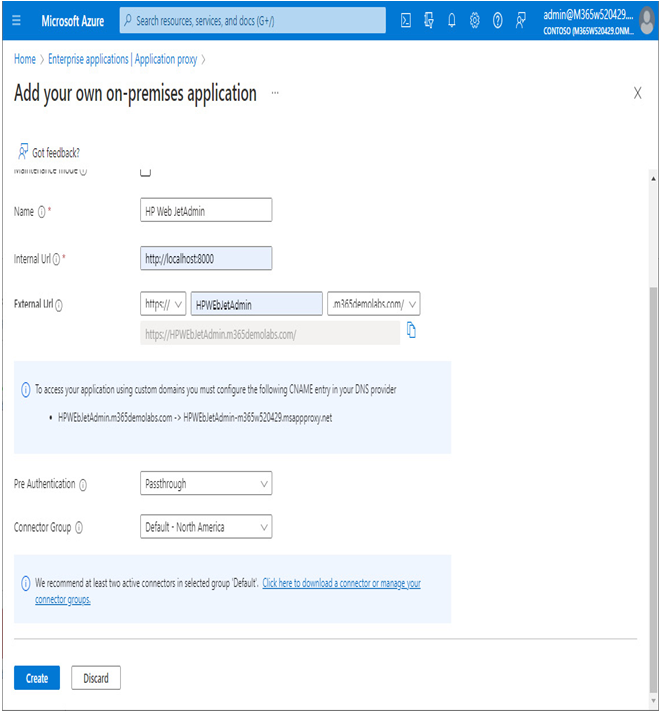
Figure 9.20 – Configuring an on-premises application
After a few moments, the Azure AD App Proxy configuration has been created.