All active, non-dismissed risks contribute to an individual user’s risk level, which equates to the probability that a user has been compromised. Risk remediation involves reviewing the logs and reports available and then making decisions on how to proceed: reset passwords, block accounts from logging in, disable the users’ devices, revoke any sign-in tokens, or confirm that the account is safe.
Implementing and managing Identity Protection
Identity Protection has three policy configuration nodes in the Identity Protection blade:
- User risk policy
- Sign-in risk policy
- Multifactor authentication registration policy
The Identity Protection User risk policy area is used to scope various Identity Protection features and enable the settings to control access enforcement:
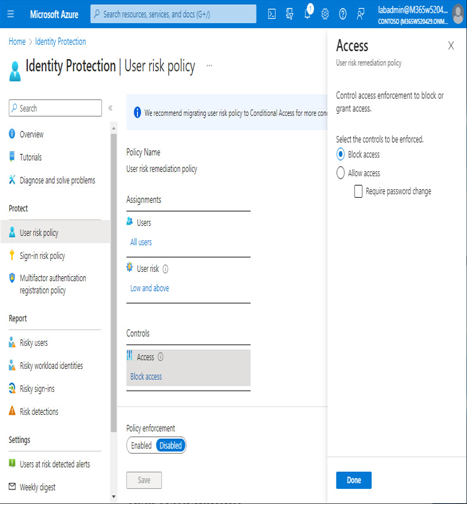
Figure 8.30 – User risk policy
The Sign-in risk policy area features similar scoping and control policy settings, as shown in Figure 8.31:
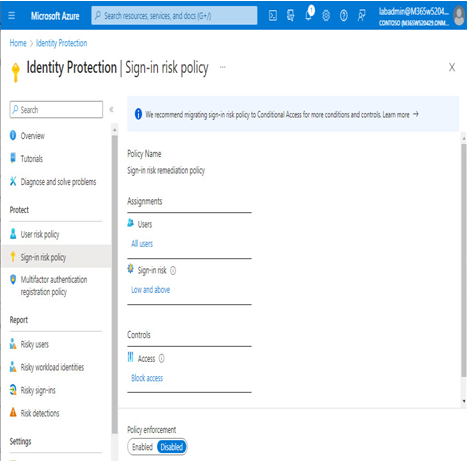
Figure 8.31 – Sign-in risk policy
Finally, the Multifactor authentication registration policy area’s controls can be used to configure Azure AD multi-factor authentication as part of self-remediation for at-risk users:
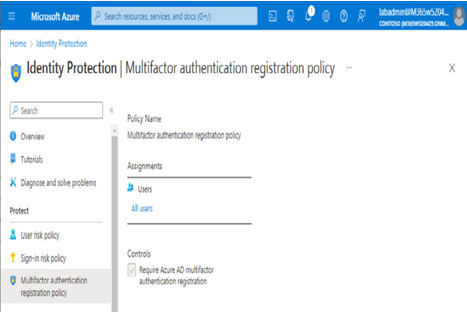
Figure 8.32 – Multifactor authentication registration policy
Microsoft recommends migrating the native Identity Protection policies to Conditional Access policies, as shown in Figure 8.33:
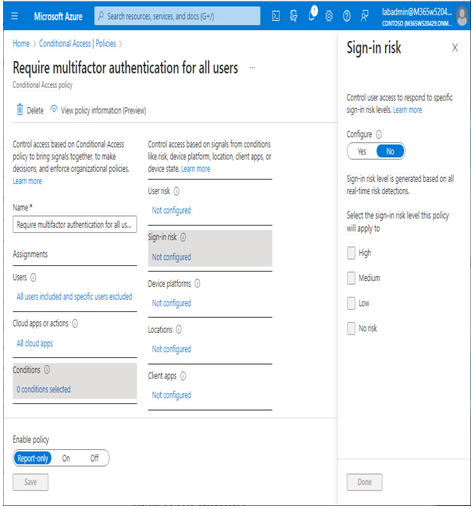
Figure 8.33 – Migrating Identity Protection policies to Conditional Access
Next, we’ll look at securing access with Conditional Access policies.
Working with secure access
With the increase in hybrid and remote work, ensuring users can securely access organization resources is more important than ever. Conditional Access policies, part of Azure AD Premium Plans P1 and P2, Enterprise Mobility + Security E3 and E5, and Microsoft 365 F1, E3, and E5, are Microsoft’s recommended way to provide identity security for Microsoft 365 users.
In this section, we’ll look at planning and configuring Conditional Access to secure identity and resources.