Conditional Access policies can be used to secure Microsoft 365 workloads and applications that are federated with Azure AD:
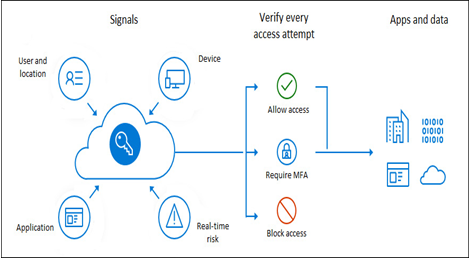
Figure 8.34 – Conditional access signals
Conditional Access requires Azure AD Premium Plan P1 for all features, except for risk-based Conditional Access, which requires Azure AD Premium Plan P2. Administering and configuring Conditional Access requires either the Global Administrator, Conditional Access Administrator, or Security Administrator role.
A Conditional Access policy is made up of the following components:
- Assignments
- Conditions
- Access controls
Let’s explore each of these areas.
Assignments
Assignments are used to control the scoping of a policy. The Users assignment control includes users, groups, and directory roles.
The Cloud apps or actions assignment is used to select which cloud apps, user actions, or authentication contexts are included or excluded. If you’re selecting cloud apps, you can choose any enterprise application that is connected to Azure AD. If you’re selecting user actions, you can include the Register security information and Register or join devices actions. You can also select an authentication context – a configuration object that is used to identify and secure content inside SharePoint.
Further reading
For more information on authentication contexts, see https://aka.ms/authentication-context.
Conditions
Conditions are the scenarios under which access will be granted or blocked. Conditions include User risk, Sign-in risk, Device platforms, Locations, Client apps, and Filter for devices. You can configure one or more conditions as part of a policy.
Access controls
Access controls are used to specify how access is granted and what experiences are allowed. Access controls are divided between Grant and Session.
The Grant configuration node is used to either block access if the conditions are met or grant access with certain stipulations: Require multifactor authentication, Require authentication strength, Require device to be marked as compliant, Require Hybrid Azure AD joined device, Require approved client app, Require app protection policy, or Require password change. You can choose to require only a single control or require all of the selected controls.
The Session configuration node controls are used to enable or manage limited experiences in supported cloud applications. You can choose to Use app enforced restrictions (only available in Office 365, Exchange Online, and SharePoint Online), Use Conditional Access App control, Sign-in frequency, Persistent browser session, Customize continuous access evaluation, Disable resilience defaults, or Require token protection for sign-in sessions.
You can configure both Grant and Session controls.
Further reading
For more information on session controls, see https://aka.ms/caapprestrictions.
Finally, as part of the planning process, you can choose to enable a policy in Report-only mode. That way, you can configure the settings and then review the sign-in logs to see whether the policy would have been applied during a particular sign-in or access attempt.